Last week, William de Groot, a digital forensics consultant discovered a protocol flaw in MySQL, which he alleges is the main reason behind e-commerce and government sites getting hacked via the Adminer database tool. He stated that Adminer can be “lured to disclose arbitrary files” which attackers can then misuse to fetch passwords for popular apps such as Magento and WordPress, thus gaining control of a site’s database. Because of this flaw, MySQL client allows MySQL server to request any local file by default.
He further states that an example of such a malicious MySQL server can be found at GitHub that was “likely used to exfiltrate passwords from these hacked sites”. A reddit user also pointed out that flaw could be further exploited to steal SSH keys and crypto wallets. The only check mark is that the server has to know the full path of the file on the client to exploit this flaw. Unlike Adminer, several clients and libraries including Golang, Python, PHP-PDO, have built-in protection for this “feature” or disable it by default.
This flaw is surprisingly a part of MySQL documentation which states:
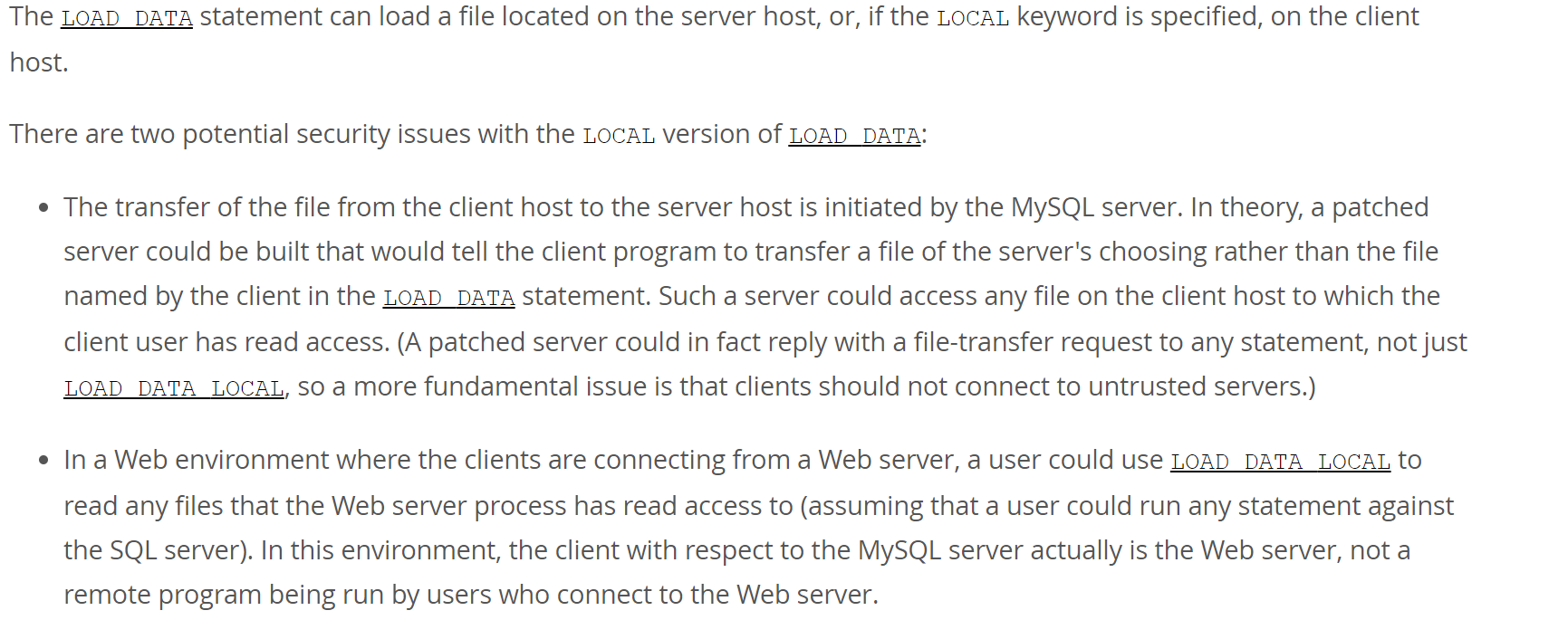 Source: MySQL Documentation
Source: MySQL Documentation
You can head over to Willem Groot’s blog for more insights on this news. Alternatively, head over to his Twitter thread for a more in-depth discussion on the topic.
Read Next
How to optimize MySQL 8 servers and clients
6 reasons to choose MySQL 8 for designing database solutions
12 most common MySQL errors you should be aware of










![How to create sales analysis app in Qlik Sense using DAR method [Tutorial] Financial and Technical Data Analysis Graph Showing Search Findings](https://hub.packtpub.com/wp-content/uploads/2018/08/iStock-877278574-218x150.jpg)





