The National Security Agency (NSA) will be publicly releasing their reverse engineering framework called GHIDRA, for the first time at the RSA Conference (Rivest, Shamir, and Adleman security conference) to be held in March 2019.
According to the official announcement on the RSA blog, the framework will be introduced by NSA’s Senior Advisor Robert Joyce. According to NSA, GHIDRA has ‘an interactive GUI capability that enables reverse engineers to leverage an integrated set of features that run on a variety of platforms including Windows, Mac O, and LINUX and supports a variety of processor instruction sets’.
This is what we know about GHIDRA so far:
- In March 2017, WikiLeaks leaked CIA Vault 7 documents which highlighted the various tools utilized by the CIA. The leaked documents included numerous references to a reverse engineering tool called ‘GHIDRA’ that was developed by the NSA at the start of the 2000s.
- For the past few years GHIDRA has been shared with other US government agencies with cyber teams that look at the inner workings of malware strains or suspicious software.
- GHIDRA is a ‘disassembler’ that breaks down software into its assembly code so that humans can analyze malware and other suspected malicious software.
- GHIDRA is built in Java, that runs on Linux, Mac and Windows operating systems and has a graphical user interface.
- With GHIDRA, developers can analyze the binaries of all major operating systems, including mobile platforms like Android and iOS.
- NSA is expected to add GHIDRA on NSA’s code repository hosted by Github where the spy agency has released several other open source programs.
Some people who are familiar with this tool and have shared opinions on HackerNews, Reddit, and Twitter. They have compared GHIDRA with IDA, another well-known reverse engineering tool.
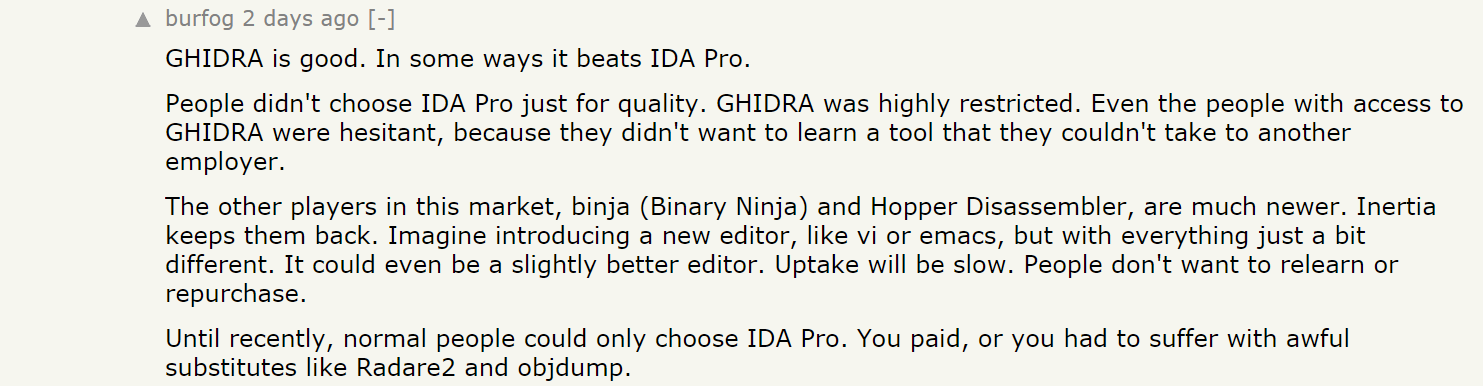
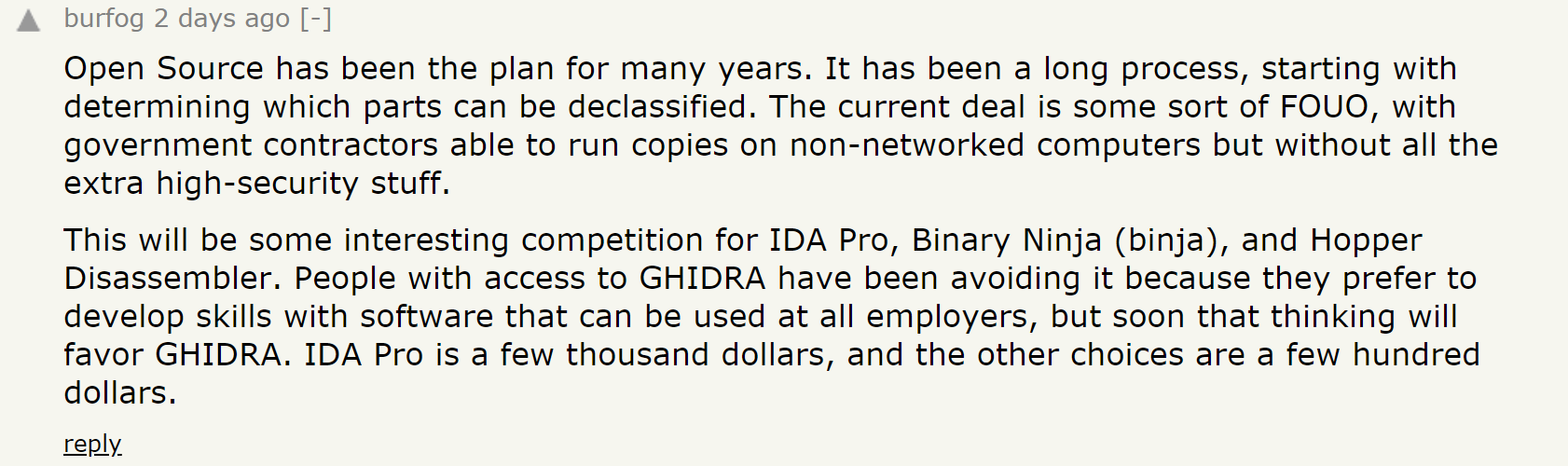
Source: HackerNews
Head over to RSA’s official blog to check out the announcement. Alternatively, check out Siliconangle for more insights on this news.
Read Next
NSA’s EternalBlue leak leads to 459% rise in illicit crypto mining, Cyber Threat Alliance report
NSA researchers present security improvements for Zephyr and Fucshia at Linux Security Summit 2018










![How to create sales analysis app in Qlik Sense using DAR method [Tutorial] Financial and Technical Data Analysis Graph Showing Search Findings](https://hub.packtpub.com/wp-content/uploads/2018/08/iStock-877278574-218x150.jpg)


