As a student, professional or enthusiast who is interested in the field of computer networking, it is quite important to have a firm understanding and the need for logical (internal) ports on an operating system and protocols.
This article is an excerpt taken from the book CompTIA Network+ Certification Guide written by Glen D. Singh and Rishi Latchmepersad. This book will help you understand topics like network architecture, security, network monitoring, troubleshooting and much more.
This article provides you with an introduction to understanding network port numbers, TCP, UDP, and ICMP.
The term “ports” or “network ports” usually means the physical interfaces or ports on a device, such as a router, switch, server or even a personal computer. However, even though these are the physical ports, there are also logical ports within an operating system or a device. You may ask yourself, how does a physical port exist within a computer, server or a network appliance such as a router or switch? Here, we are going to further breakdown the concepts of these logical ports or what is known as network ports.
To get started, we will use a simple analogy to help you understand the fundamentals of logical ports on a system. Let’s imagine you own an organization, at the headquarters location, is a single building with many floors and at the center of the building are the elevators for easy access to the upper floors. Each floor is occupied by a unique department and its respective staff members of the organization. Each day, the employees use the elevators which transport the staff to his/her relevant department and back. Let’s imagine the physical building is a computing system such as a server, there are doors at each relevant department and the employees of the organization are different types of network traffic entering and leaving the system on a daily basis.
Now let’s put all the piece together and get everything working in harmony. Each time an employee (network traffic) enters the building (operating system), he/she takes the elevator (Transport Layer) which delivers the employee to their respective doorway (logical port) at their department (service/protocol at the Application Layer). From this analogy, you may have realized each type of network traffic (employee) enters their relevant department using a doorway, this doorway is a logical port existing within the operating system (building) and won’t be visible to any entity outside of the system.
Each type of network traffic is sent to a specific logical port for further processing before it’s delivered to the Application Layer.
The Internet Assigned Numbers Authority (IANA) is the governing body who manages and regulates Internet Protocol (IP) addresses and Port Numbers assignments. According to the Service Name and Transport Protocol Port Number Registry of IANA, there are a total of 65,535 ports. Each of which is either Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) port types, there are some ports which are both TCP and UDP types.
The ranges of the ports are categorized into three simple categories for easy identification:

[box type=”shadow” align=”” class=”” width=””]Get further information on the assignments of port by Internet Assigned Numbers Authority (IANA) on its official website.[/box]
Internet Engineering Task Force (IETF) defines the procedures for managing the service names and port numbers by RFC 6335. Now we have a clear understanding of the roles of ports on a system, let’s dive a bit deeper in define some of the well-known ports and their purposes on a network.
Network Protocols and their Port numbers
A network protocol defines the rules and procedures in which data communication occurs between devices over a network. Without predefined rules or procedures, the messages traversing a network would be without any particular formatting and may not be meaningful to the receipt device. To further discuss the importance of have protocols on a network/system, we will use the following analogy to provide you with a real-world situation in comparison to network protocols.
Let’s imagine you work for an organization, ACME Corp and within the company, there are many policies and procedures that govern the handling of day to day transactions and activities within the organization. One of the most important procedure is the emergency evacuation plan. If there’s an emergency with the organization, the procedure documents the rules and guidelines each employee must follow to ensure they are escorted safely out the compound unto the muster point while the health and safety officers conduct their checks before allowing anyone to re-enter the compound. If proper procedures and guidelines didn’t exist within ACME Corp, persons would be attempt exist the compound in a haphazard behavior which may result in further safety issues. With procedures and guidelines, the employees evacuate in a systematic manner.
This is the same concept which is applied on the network. There are many different protocols which use a network to communicate with another device. Each protocol has their own uniqueness in which the information is formatted, the rules and procedures it follows while traveling on the network until it is received by the intending receipt and process upwards on the Open Systems Interconnection (OSI) reference model or the Transmission Control Protocol/Internet Protocol (TCP/IP) stack.
[box type=”shadow” align=”” class=”” width=””]The ISO Open Systems Interconnection (OSI) is simply a reference model and it not actually implemented on a system, however, network professionals use this model mostly during network and security discussions and troubleshooting concepts. The Transmission Control Protocol/Internet Protocol (TCP/IP) stack is implemented in all network related devices.[/box]
Now you have understood the concepts of network protocols, let’s discuss some of the popular protocols and their respective port numbers and their importance on a network.
Protocol Types
Internet Control Message Protocol (ICMP)
On a network, whether on a Local Area Network (LAN) or a Wide Area Network (WAN), host devices will be communicating to exchange data and information between each other and sometimes an error can occur. Let’s imagine you are sending a packet to a server on the internet, while your computer is initializing the connection between itself and the remote server, it provides an error stating unable to connect. As an upcoming networking professional, you may wonder why both devices are unable to successfully establish a connection amongst themselves.
Internet Control Message Protocol (ICMP) defined by RFC 792 is typically used to provide error reporting on a network. There are many types of Internet Control Message Protocol (ICMP) messages which provide different actions and give feedback if an error occurs, and also the issue which exists.
Internet Control Message Protocol (ICMP) Message Types
There are many Internet Control Message Protocol (ICMP) message types however, we’ll be discussing the main ones which will be very useful as a network professional.
ICMP Type 0 – Echo Reply
The Type 0 message is when a sender device is responding to an ICMP Type 8, Echo request.
ICMP Type 3 – Destination Unreachable
Type 3 is given then a destination cannot be found or is simply unreachable by the sender. However, ICMP Type 3 gives a bit more details by adding a Code to the message.
- Code 0 – Network Unreachable
- Code 1 – Host Unreachable
- Code 2 – Protocol Unreachable
- Code 3 – Port Unreachable
Therefore combining the ICMP Type 3 message with a unique Code gives you, the network professional a better idea to the error on the network.
ICMP Type 5 – Redirect
An ICMP Type 5 message occurs when a default gateway device such as a router notifies the sender to send the traffic directly to another gateway which exists on the same network. One reason can the second gateway device or router may have a better route to the destination or a shorter path.
ICMP Type 8 – Echo Request
The ICMP Type 8 message is used by a sender device to check for basic network connectivity between itself and the intended recipient device. Any device receiving an ICMP Type 8 message, responds with an ICMP Type 0 – Echo Reply.
ICMP Type 11 – Time Exceeded
Type 11 is given the Time to Live (TTL) expires or reaches zero (0) before reaching the intended recipient device. The last gateway which adjusts the TTL to zero (0) notified the sender using an ICMP Type 11 message as displayed below:
The -i parameter adjusts the Time To Live (TTL) value on the ICMP message.
C:\>ping 8.8.8.8 -i 4Pinging 8.8.8.8 with 32 bytes of data:
Reply from 179.60.213.149: TTL expired in transit.
Reply from 179.60.213.66: TTL expired in transit.
Reply from 179.60.213.66: TTL expired in transit.
Reply from 179.60.213.66: TTL expired in transit.
Ping statistics for 8.8.8.8:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),Without adjusting the Time To Live (TTL) value of the ICMP Type 8 message, the sender received an ICMP Type 0 messages indicating successful transmission between both devices.
C:\>ping 8.8.8.8Pinging 8.8.8.8 with 32 bytes of data:
Reply from 8.8.8.8:
bytes=32 time=52ms TTL=120
Reply from 8.8.8.8: bytes=32 time=52ms TTL=120
Reply from 8.8.8.8: bytes=32 time=52ms TTL=120
Reply from 8.8.8.8: bytes=32 time=52ms TTL=120
Ping statistics for 8.8.8.8:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milliseconds: Minimum = 52ms, Maximum = 52ms, Average = 52ms[box type=”shadow” align=”” class=”” width=””]Further information of Internet Control Message Protocol (ICMP) can also be found at: https://tools.ietf.org/html/rfc792. Further information of all the Internet Control Message Protocol (ICMP) message types can be found at: https://www.iana.org/assignments/icmp-parameters/icmp-parameters.xhtml#icmp-parameters-codes-7.[/box]
A simple and easy-to-use utility is Ping. The Ping utility harnesses the functionality of Internet Control Message Protocol (ICMP) and provides meaningful feedback whether communication is successful, unsuccessful, redirected, the destination host or network is unreachable, etc. The Ping utility is integrated into almost every, if not all modern day operating systems, from desktops, servers, and even mobile operating systems.
The ping command can be executed in the Windows Command Prompt or the Terminal of Linux-based Operating Systems. When a user initiates the ping command with a destination address, the ping utility would send an ICMP Type 8 message to the intended destination. The syntax for checking basic connectivity is as follows:
ping <ip address or hostname>
ping 8.8.8.8
ping www.google.comTransmission Control Protocol (TCP)
When you send a letter using your local postal service, have you ever wondered if your letter reaches the destination successfully, was your letter prioritized within the processing system of the mail service for delivery or what confirmation would you receive when the letter the is delivered successfully? Imagine in a network, these are the same concerns with devices. If one device sends a datagram to another device, whether one the same Local Area Network (LAN) or a remote network, what reassurance is given for the guarantee of the datagram (message) between sender and the receiver?
Transmission Control Protocol (TCP) defined by RFC 793 is a connection-oriented protocol which operates are the Transport Layer of both the Open Systems Interconnection (OSI) reference model and the Transmission Control Protocol/Internet Protocol (TCP/IP) protocol stack. It is designed to provide reliable transportation of the datagrams over a network. It provides reassurance by initializing a 3-way handshake before communicating data between the sender the receiver. Let’s imagine there are two (2) devices who wants to communicate and use TCP to ensure their messages are delivered successfully. Let’s use a simple analogy to further explain the TCP 3-Way Handshake, we have two (2) device, Bob and Alice. Bob wants to exchanges data with Alice but needs to ensure the data being sent are successfully delivered, so Bob decides to use the Transmission Control Protocol (TCP) to guarantee the delivery.
Bob initializes the TCP 3-Way Handshake by sending a TCP Synchronization (SYN) packet to Alice indicating he wants to establish a session or connection. Alice, upon receiving the SYN packet, responds to Bob indicating she also wants to establish a session and acknowledges receipt of the SYN packet using a TCP Synchronization and Acknowledgment (SYN/ACK) packet. Bob, upon receiving the TCP SYN packet from Alice, responds with a TCP Acknowledgement (ACK) packet. Now the TCP 3-Way Handshake is established, data can be exchanged between the two (2) devices, each datagram sent across the session between Bob and Alice, an ACK packet will be sent to confirm successful delivery of the message.

What if Bob sends a message to Alice, and Bob does not receive an ACK from Alice? In this situation, Bob would retransmit the data again after certain intervals until an ACK packet is sent back to Bob. Another question you may have is, how does Transmission Control Protocol (TCP) terminates a session gracefully? Each device sends a TCP Finish (FIN) packet to each other indicating they would like to terminate the session.

Furthermore, if we use a network protocol analyzer tools such as Wireshark, we can see the packet composition of each datagram passing across the network. The following exhibit is a capture using Wireshark during the writing of this book to demonstrate the TCP 3-Way Handshake.
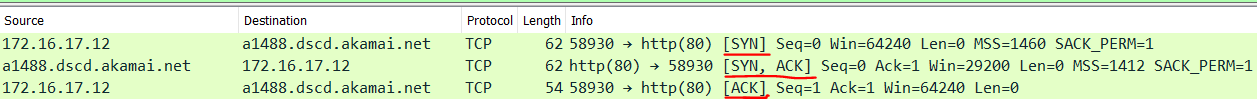
[box type=”shadow” align=”” class=”” width=””]Reassemble packet in order[/box]
User Datagram Protocol (UDP)
User Datagram Protocol (UDP), defined by RFC 768 is a connectionless protocol. This protocol also operates at the Transport Layer of both the Open Systems Interconnection (OSI) reference model and the Transmission Control Protocol/Internet Protocol (TCP/IP) protocol stack. However, unlike Transmission Control Protocol (TCP), the User Datagram Protocol (UDP) does not provide any guarantee or reassurance of the delivery of datagrams across a network. Not all protocols at the Application Layer uses TCP, there are many Layer 7 protocols which uses the User Datagram Protocol (UDP).
You may be wondering, why would an upper layer protocol uses UDP instead of TCP? Let do a brief recap of TCP, when devices are using TCP as their preferred Transport Layer protocol, each message sent between the sender and the receiver, an Acknowledge (ACK) packet is returned. This means if a sender such as Bob, sends one hundred (100) packets to Alice over the network, Alice would return one hundred (100) Acknowledgment (ACK) packets to Bob. Let’s imagine a larger network with hundreds, thousands or even the Internet, where everyone would use TCP, the returned traffic, in this case, would the ACK packets, would create a lot of overhead in the network and therefore cause congestion. This is a bit similar to having a roadway and the number of vehicles are increasing, this would cause traffic.
Let’s use another analogy, a lot of persons globally uses YouTube for many reasons. Imagine if the video traffic uses TCP instead of UDP, YouTube has millions of users daily who streams content on the site. If each user were to send a TCP ACK packet back to YouTube on that very large scale, the YouTube network and even the Internet would be congested with a lot of TCP ACK packets and would cause the network performance to degrade. Therefore, not all upper layer protocols use TCP because of this issue.
The way in which UDP behaves is simply sending datagrams without any reassurance or guarantee delivery of the message. When devices are communicating over a network, the path with each packet may take may be different from the other and therefore may be received in an out-of-order sequence. The User Datagram Protocol (UDP) does not provide any mechanisms for reassembly of the packet unlike the Transmission Control Protocol (TCP) which aids in the reassembly and reordering of the packets when they are received from the sender.
[box type=”shadow” align=”” class=”” width=””]Voice and video traffic use UDP as the preferred Transport Layer protocol.[/box]
Comparison of TCP and UDP
Transmission Control Protocol (TCP)
- Reliable
- Uses Acknowledgments to confirm receipt of data
- Re-sends data of any of the packets are lost during transmission
- Delivers the data in sequential order and handles reassembly
- Applications: HTTP, FTP, SMTP, Telnet.
User Datagram Protocol (UDP)
- Very fast in delivery of data
- Very low overhead on the network
- Does not require any acknowledgment packets
- If packets are lost during transmission, it does not resend any lost data
- Does not send data in order or handles the reassembly
- Applications: DHCP, DNS, SNMP, TFTP, VoIP, IPTV.
[box type=”shadow” align=”” class=”” width=””]There are protocols which uses both TCP and UDP such as DNS and SNMP.[/box]
Internet Protocol (IP)
Internet Protocol (IP) defined by RFC 791 was created for operations in interconnected systems of packet-switched computer communication networks. Internet Protocol (IP) operates at the Network Layer of the Open Systems Interconnection (OSI) reference model and the Internet Layer of the Transmission Control Protocol/Internet Protocol (TCP/IP) protocol suite.
However, Internet Protocol (IP) has three main characteristics:
- Connectionless – The sender of the message does not know if the recipient is available or not, the protocol sends the messages as is. If the message is successfully delivered to the intended recipient, the sender does not know if the message arrives or not. Since IP behaves a bit like UDP, there is not session create prior to the data communication, which leads to the receiver is not aware of any incoming messages.
- Uses Best Effort – Best Effort implies that Internet Protocol (IP) is unreliable. Similarly to UDP, Internet Protocol (IP) does not provide any guarantee of the data between a sender and receiver. Furthermore, if any data is lost during the transmission, IP does not have the functionality to facilitate the resending of any lost packets.
- Media Independent – The benefit of using Internet Protocol (IP) is, it is independent of the type of media being used for transporting the data between the sender and the receiver. At times, there are many different types of media between the sender and the receiver, such as copper cables, radio frequency, fiber optic, etc. Internet Protocol (IP) datagrams can be transported over any media type, the Data Link is responsible for formatting the Frame for each type of media as it leaves a device.
Thus, in this article, we learned about the network port numbers and also about the different protocol types in detail. If you’ve enjoyed reading this article, and want to get a better understanding of the Network+ Certification read our book, CompTIA Network+ Certification Guide.
Read Next
Bo Weaver on Cloud security, skills gap, and software development in 2019
What matters on an engineering resume? Hacker Rank report says skills, not certifications
Wolf Halton on what’s changed in tech and where we are headed










![How to create sales analysis app in Qlik Sense using DAR method [Tutorial] Financial and Technical Data Analysis Graph Showing Search Findings](https://hub.packtpub.com/wp-content/uploads/2018/08/iStock-877278574-218x150.jpg)







![Using Python Automation to interact with network devices [Tutorial] Why choose Ansible for your automation and configuration management needs?](https://hub.packtpub.com/wp-content/uploads/2018/03/Image_584-100x70.png)

