This article is an excerpt taken from the book, Hands-On Cybersecurity for Finance written by Dr. Erdal Ozkaya and Milad Aslaner. In this book you will learn how to successfully defend your system against common cyber threats, making sure your financial services are a step ahead in terms of security.
In this article, you will understand the different types of threat actor groups and their motivations.
The attackers behind cyber attacks can be classified into the following categories:
- Cybercriminals
- Cyber terrorists
- Hacktivists
“What really concerns me is the sophistication of the capability, which is becoming good enough to really threaten parts of our critical infrastructure, certainly in the financial, banking sector.”– Director of Europol Robert Wainwright
Hacktivism
Hacktivism, as defined by the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT), refers to threat actors that depend on propaganda rather than damage to critical infrastructures. Their goal is to support their own political agenda, which varies between anti-corruption, religion, environmental, or anti-establishment concerns. Their sub-goals are propaganda and causing damage to achieve notoriety for their cause. One of the most prominent hacktivist threat actor groups is Anonymous. Anonymous is known primarily for their distributed denial of service (DDoS) attacks on governments and the Church of Scientology. The following screenshot shows “the man without a head,” which is commonly used by Anonymous as their emblem:

Hacktivists target companies and governments based on the organization’s mission statement or ethics. Given that the financial services industry is responsible for economic wealth, they tend to be a popular target for hacktivists.
The ideologies held by hacktivists can vary, but at their core, they focus on bringing attention to social issues such as warfare or what they consider to be illegal activities. To spread their beliefs, they choose targets that allow them to spread their message as quickly as possible. The primary reason why hacktivists are choosing organizations in the financial services industry sector is that these organizations typically have a large user base, allowing them to raise the profile of their beliefs very quickly once they have successfully breached the organization’s security controls.
Case study – Dakota Access Pipeline
The Dakota Access Pipeline (DAPL) was a 2016 construction of a 1.172-mile-long pipeline that spanned three states in the US. Native American tribes were protesting against the DAPL because of the fear that it would damage sacred grounds and drinking water. Shortly after the protests began, the hacktivist group Anonymous publicly announced their support under the name OpNoDAPL. During the construction, Anonymous launched numerous DDoS attacks against the organizations involved in the DAPL. Anonymous leaked the personal information of employees that were responsible for the DAPL and threatened that this would continue if they did not quit. The following screenshot shows how this attack spread on Twitter:
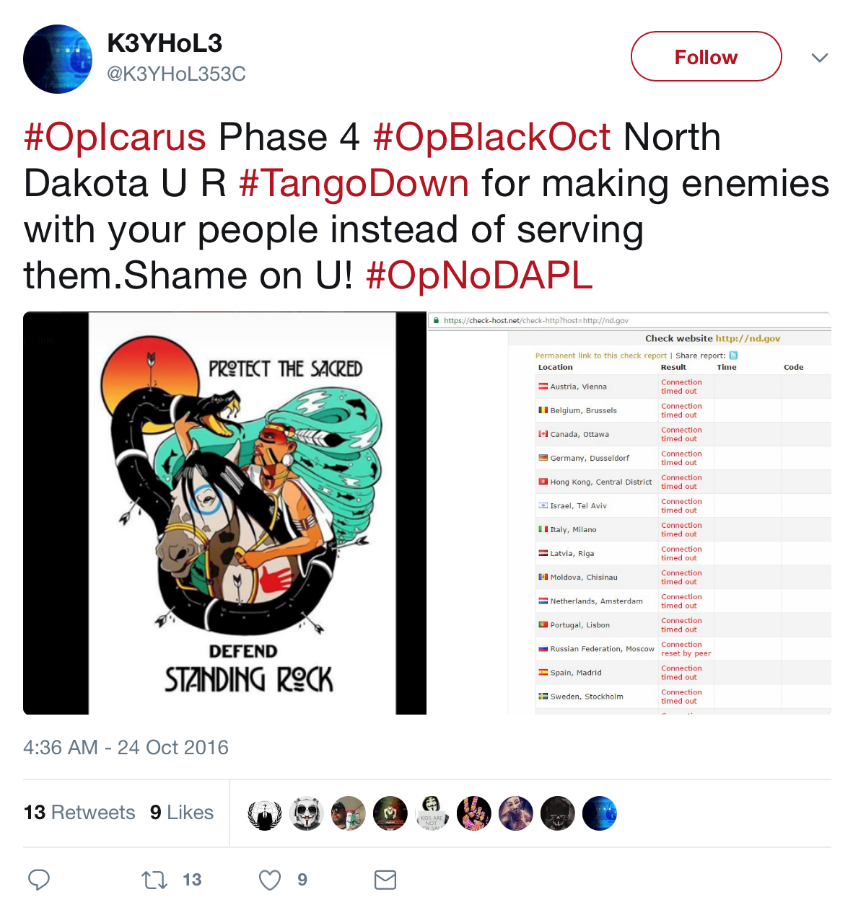
Case study – Panama Papers
In 2015, an offshore law firm called Mossack Fonseca had 11.5 million of their documents leaked. These documents contained confidential financial information for more than 214,488 offshore entities under what was later known as the Panama Papers. In the leaked documents, several national leaders, politicians, and industry leaders were identified, including a trail to Vladimir Putin. The following diagram shows how much was exposed as part of this attack:

While there is not much information available on how the cyber attack occurred, various security researchers have analyzed the operation.
According to the WikiLeaks post, which claims to show a client communication from Mossack Fonseca, they confirm that there was a breach of their “email server“. Considering the size of the data leak, it is believed that a direct attack occurred on the email servers.
Cyber terrorists
Extremist and terrorist organizations such as Al Qaeda and Islamic State of Iraq and Syria (ISIS) are using the internet to distribute their propaganda, recruiting new terrorists and communicating via this medium. An example of this is the 2008 attack in Mumbai, in which one of the gunmen confirmed that they used Google Earth to familiarize themselves with the locations of buildings. Cyber terrorism is an extension of traditional terrorism in cyber space.
Case study – Operation Ababil
In 2012, the Islamic group Izz ad-Din al-Qassam Cyber Fighters—which is a military wing of Hamas—attacked a series of American financial institutions. On September 18th 2012, this threat actor group confirmed that they were behind the cyber attack and justified it due to the relationship of the United States government with Israel. They also claimed that this was a response to the Innocence of Muslims video released by the American pastor Terry Jones. As part of a DDoS attack, they targeted the New York Stock Exchange as well as banks such as J.P. Morgan Chase.
Cyber criminals
Cyber criminals are either individuals or groups of hackers who use technology to commit crimes in the digital world. The primary driver of cyber criminals is financial gain and/or service disruption. Cyber criminals use computers in three broad ways:
- Select computers as their target: These criminals attack other people’s computers to perform malicious activities, such as spreading viruses, data theft, identity theft, and more.
- Use computers as their weapon: They use computers to carry out “conventional crime”, such as spam, fraud, illegal gambling, and more.
- Use computers as an accessory: They use computers to save stolen or illegal data.
The following provides the larger picture so we can understand how Cyber Criminals has penetrated into the finance sector and wreaked havoc:

Becky Pinkard, vice president of service delivery and intelligence at Digital Shadows Ltd, states that “Attackers can harm the bank by adding or subtracting a zero with every balance, or even by deleting entire accounts”.
Case study – FIN7
On August 1st 2018, the United States District Attorney’s Office for the Western District of Washington announced the arrest of several members of the cyber criminal organization FIN7, which had been tracked since 2015. To this date, security researchers believe that FIN7 is one of the largest threat actor groups in the financial services industry. Combi Security is a FIN7 shelf company.
The screenshot presented here shows a phishing email sent by FIN7 to victims claiming it was sent by the US Food and Drug Administration (FDA)
Case study – Carbanak APT Attack
Carbanak is an advanced persistent threat (APT) attack that is believed to have been executed by the threat actor group Cobalt Strike Group in 2014. In this operation, the threat actor group was able to generate a total financial loss for victims of more than 1 billion US dollars. The following depicts how the Carbanak cyber-gang stole $1bn by targeting a bank:

Case study – OurMine operation
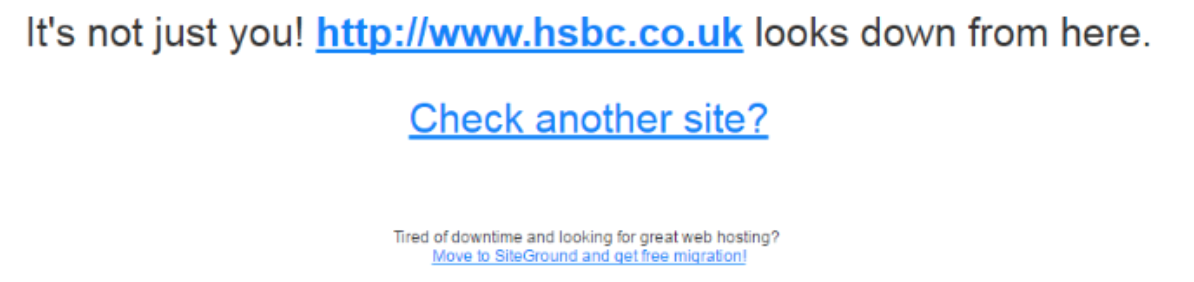
In 2016, the threat actor group OurMine, who are suspected to operate in Saudi Arabia, conducted a DDoS attack against HSBC’s websites, hosted in the USA and UK. The following screenshot shows the communication by the threat actor:

The result of the DDoS attack was that HSBC websites for the US and the UK were unavailable. The following screenshot shows the HSBC USA website after the DDoS attack:
Summary
The financial services industry is one of the most popular victim industries for cybercrime. Thus, in this article, you learned about different threat actor groups and their motivations. It is important to understand these in order to build and execute a successful cybersecurity strategy. Head over to the book, Hands-On Cybersecurity for Finance, to know more about the costs associated with cyber attacks and cybersecurity.
Read Next
RSA Conference 2019 Highlights: Top 5 cybersecurity products announced
Security experts, Wolf Halton and Bo Weaver, discuss pentesting and cybersecurity [Interview]
Hackers are our society’s immune system – Keren Elazari on the future of Cybersecurity










![How to create sales analysis app in Qlik Sense using DAR method [Tutorial] Financial and Technical Data Analysis Graph Showing Search Findings](https://hub.packtpub.com/wp-content/uploads/2018/08/iStock-877278574-218x150.jpg)







![Using Python Automation to interact with network devices [Tutorial] Why choose Ansible for your automation and configuration management needs?](https://hub.packtpub.com/wp-content/uploads/2018/03/Image_584-100x70.png)

