(For more resources on Microsoft products, see here.)
Configuring applications to run with elevated privileges on-the-fly
Despite all the possible workarounds to launch an application or set of commands with elevated privileges from a standard user account, Windows doesn't provide any built-in means of allowing system administrators to configure a particular application to launch as the currently logged in standard user, but with an administrative token. Consider a situation where you don't have time to fix an application that won't run as a standard user, but don't want to grant administrative privileges just for the sake of one application. While it may be possible to start the application using a secondary logon, this is impractical in most cases.
Solving LUA problems with Avecto Privilege Guard
Privilege Guard is a third-party solution, from Microsoft Gold Partner Avecto, that allows system administrators to dynamically add or remove privileges by modifying the logged in user's access token as it's assigned to new processes. The client-side component, provided as an .exe or .msi file for GPSI deployment, is implemented as a user-mode service and supports Windows XP (or Windows Server 2003) and later. Privilege Guard is licensed on a trust model, so it doesn't adhere to a strict object count in Active Directory.
Client settings are deployed with User or Computer Group Policy using a flexible architecture that separates policies, applications, messaging and access tokens. Programs can also be grouped together to minimize the number of policies applied.
Defining application groups
For each Application Group, you can define one or more programs using the following categories:
- Executables
- Control Panel Applets
- Management Console snap-ins
- Windows Installer Packages
- Windows Scripting Host (WSH), PowerShell scripts and batch files
- Registry Editor files
- ActiveX controls (matched by URL or CLSID)
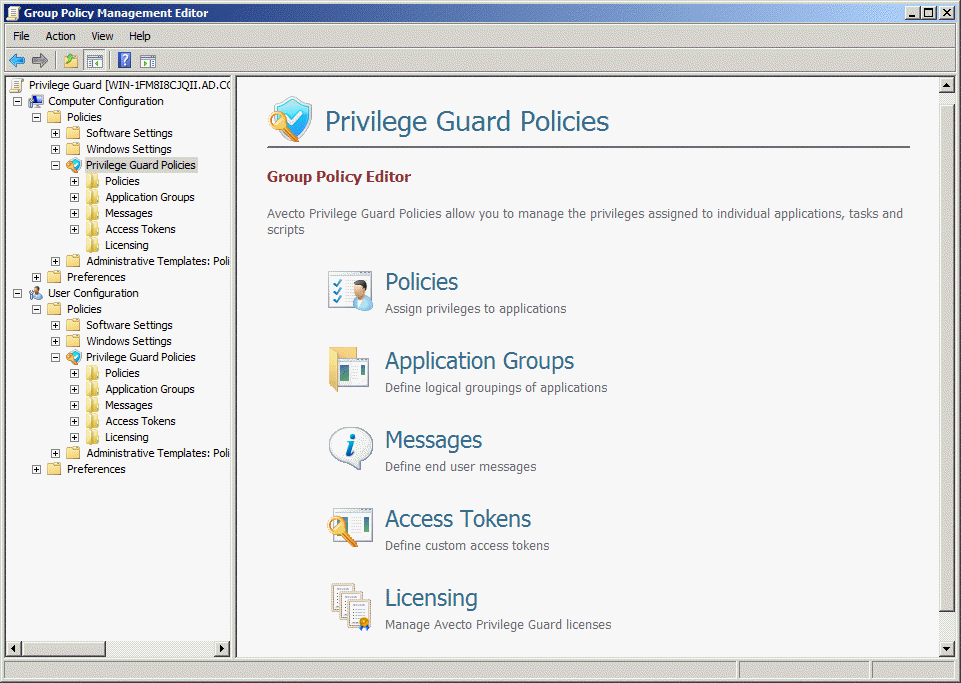
Application Templates can also be used to quickly locate built-in Windows tools such as Performance Monitor or System Restore. In the screenshot that follows, I used an Application Template to locate the Disk Management console (diskmgmt.msc) in Windows 7. The default setting is to match processes by file or folder name, but processes can also be matched by command line switch, file hash, publisher or any combination thereof. Privilege Guard supports matching by publisher certificate when Windows binaries are indirectly signed using Windows Security Catalogs.
Unlock access to the largest independent learning library in Tech for FREE!
Get unlimited access to 7500+ expert-authored eBooks and video courses covering every tech area you can think of.
Renews at $19.99/month. Cancel anytime
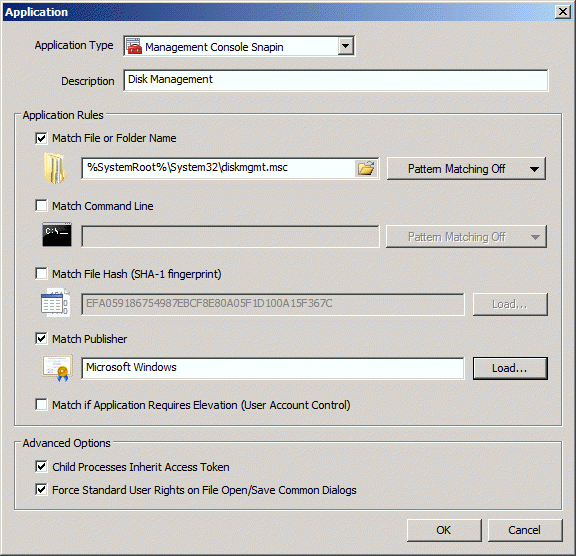
Additional options include:
- The ability to match processes if Privilege Guard detects that an application will trigger UAC.
- To determine whether child processes spawned by the matched parent process inherit the privileges of the user's modified access token.
- To suppress elevated privileges on File Open/Save common dialogs to prevent users from modifying protected files.
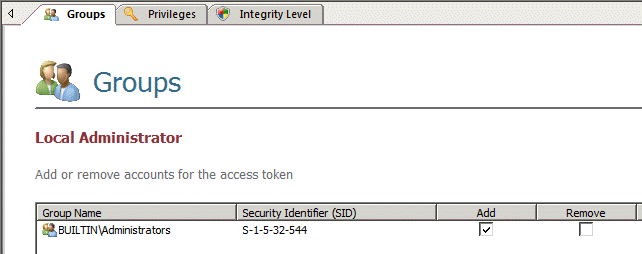
Defining access tokens
We can define the rights allotted to access tokens in Privilege Guard based on the privileges assigned to Windows built-in groups. Rights can also be added or removed on an individual basis. The access token below uses the built-in Administrators group as the basis for assigning privileges.
An access token's integrity level can also be overridden.
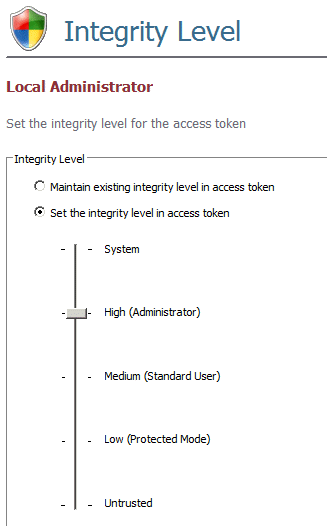
Any combination of groups, privileges or integrity levels can be added or removed in an access token.
 United States
United States
 Great Britain
Great Britain
 India
India
 Germany
Germany
 France
France
 Canada
Canada
 Russia
Russia
 Spain
Spain
 Brazil
Brazil
 Australia
Australia
 Singapore
Singapore
 Canary Islands
Canary Islands
 Hungary
Hungary
 Ukraine
Ukraine
 Luxembourg
Luxembourg
 Estonia
Estonia
 Lithuania
Lithuania
 South Korea
South Korea
 Turkey
Turkey
 Switzerland
Switzerland
 Colombia
Colombia
 Taiwan
Taiwan
 Chile
Chile
 Norway
Norway
 Ecuador
Ecuador
 Indonesia
Indonesia
 New Zealand
New Zealand
 Cyprus
Cyprus
 Denmark
Denmark
 Finland
Finland
 Poland
Poland
 Malta
Malta
 Czechia
Czechia
 Austria
Austria
 Sweden
Sweden
 Italy
Italy
 Egypt
Egypt
 Belgium
Belgium
 Portugal
Portugal
 Slovenia
Slovenia
 Ireland
Ireland
 Romania
Romania
 Greece
Greece
 Argentina
Argentina
 Netherlands
Netherlands
 Bulgaria
Bulgaria
 Latvia
Latvia
 South Africa
South Africa
 Malaysia
Malaysia
 Japan
Japan
 Slovakia
Slovakia
 Philippines
Philippines
 Mexico
Mexico
 Thailand
Thailand



















