Creating Certificates
One method could be setting up tunnels using pre-shared keys with static encryption, however, X509 certificates provide a much better level of security than pre-shared keys do. There is, however, slightly more work to be done to set up and connect two systems with certificate-based authentication. The following five steps have to be accomplished:
- Create a CA certificate for your CA with which we will sign and revoke client certificates.
- Create a key and a certificate request for the clients.
- Sign the request using the CA certificate and thereby making it valid.
- Provide keys and certificates to the VPN partners.
- Change the OpenVPN configuration so that OpenVPN will use the certificates and keys, and restart OpenVPN.
There are a number of ways to accomplish these steps. easy-rsa is a command-line tool that comes with OpenVPN, and exists both on Linux and Windows. On Windows systems you could create certificates by clicking on the batch files in the Windows Explorer, but starting the batch files at the command-line prompt should be the better solution. On Linux you type the full path of the scripts, which share the same name as on Windows, simply without the extension .bat.
Certificate Generation on Windows XP with easy-rsa
Open the Windows Explorer and change to the directory C:Program Files OpenVPNeasy-rsa. The Windows version of easy-rsa consists of thirteen files. On Linux systems you will have to check your package management tools to find the right path to the easy-rsa scripts. On Debian Linux you will find them in /usr/share/doc/openvpn/examples/easy-rsa/.
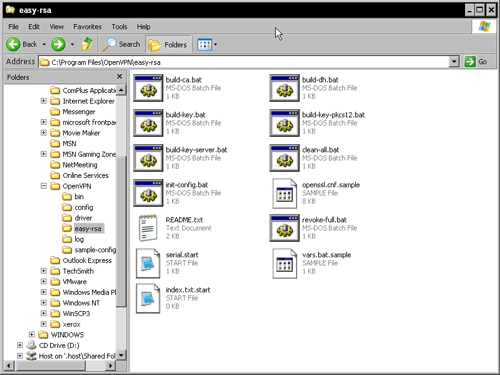
You find there are eight batch files, four configuration files, and a README (which is actually not really helpful). However, we must now create a directory called keys, copy the files serial.start and index.txt.start into it, and rename them to serial and index.txt respectively. The keys and certificates created by easy-rsa will be stored in this directory. These files are used as a database for certificate generation.
Now we let easy-rsa prepare the standard configuration for our certificates. Double-click on the file C:Program FilesOpenVPNeasy-rsainit-config.bat or start this batch file at a command-line prompt. It simply copies the template files vars.bat.sample to vars.bat and openssl.cnf.sample to openvpn.ssl. While the file openssl is a standard OpenSSL configuration, the file vars.bat contains variables used by OpenVPN's scripts to create our certificates, and needs some editing in the next step.
Setting Variables—Editing vars.bat
Right-click on the vars.bat file's icon and select from the menu.
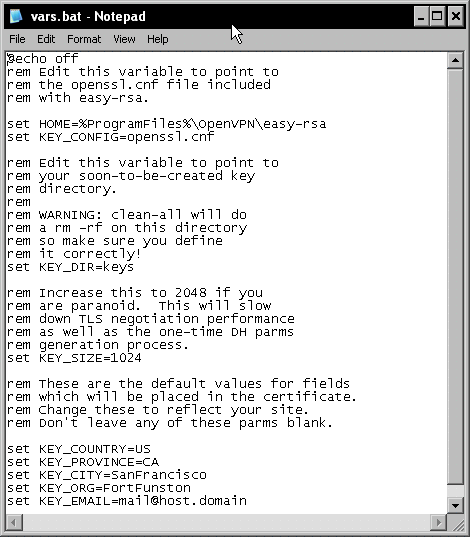
In this file, several parameters are set that are used by the certificate generation scripts later. The following table gives a quick overview of the entries in the file:
|
Entry in vars.bat
|
Function
|
|
set HOME=%ProgramFiles%OpenVPN easy-rsa
|
The path to the directory where easy-rsa resides.
|
|
set KEY_CONFIG=openssl.cnf
Unlock access to the largest independent learning library in Tech for FREE!
Get unlimited access to 7500+ expert-authored eBooks and video courses covering every tech area you can think of.
Renews at $19.99/month. Cancel anytime
|
The name of the OpenSSL configuration file.
|
|
set KEY_DIR=keys
|
The path to the directory where the newly generated keys are stored-relative to $HOME as set above.
|
|
set KEY_SIZE=1024
|
The length of the SSL key. This parameter should be increased to 2048.
|
|
set KEY_COUNTRY=US
set KEY_PROVINCE=CA
set KEY_CITY=SanFrancisco
set KEY_ORG=FortFunston
set KEY_EMAIL=mail@host.domain
|
These five values are used as suggestions whenever you start a script and generate certificates with the easy-rsa software.
|
Only the entry KEY_SIZE must be changed (unless you don't care much about security), but setting the last five entries to your needs might be very helpful later. Every time we generate a certificate, easy-rsa will ask (among others) for these five parameters, and give a suggestion that could be accepted simply by pressing Enter. The better the default values set here in vars.bat fit our needs, the less typing work we will have later. I leave it up to you to change these settings here.
The next step is easy. Run vars.bat to set the variables. Even though you could simply double-click on its explorer icon, I recommend that you run it in a shell window. Select the entry Run from Windows' main menu, type cmd.exe, and change to the easy-rsa directory by typing cd "C:Program FilesOpenVPNeasy-rsa" and pressing Enter. By doing so, we will proceed in exactly the same way as we would do on a Linux system (except for the .bat extensions).
Creating the Diffie-Hellman Key
Now it is time to create the keys that will be used for encryption, authentication, and key exchange. For the latter, a Diffie-Hellman key is used by OpenVPN. The Diffie-Hellman key agreement protocol enables two communication partners to exchange a secret key safely. No prior secrets or safe lines are needed; a special mathematical algorithm guarantees that only the two partners know the used shared key. If you would like to know exactly what this algebra is about, have a look at this website: http://www.rsasecurity.com/rsalabs/node.asp?id=2248.
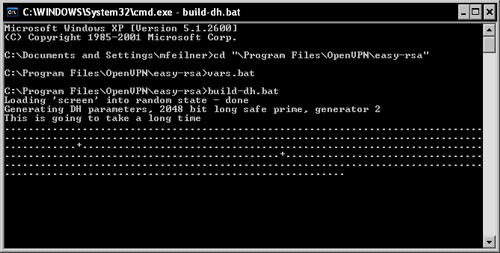
easy-rsa provides a script (batch) file that generates the key for you: C:Program FilesOpenVPNeasy-rsabuild-dh.bat. Start it by typing build-dh.bat. A Diffie-Hellman key is being generated. The batch file tells you, This is going to take a long time, which is only true if your system is really old or if you are not patient enough. However, on modern systems some minutes may be a time span horribly long!
Building the Certificate Authority
OK, now it's time to generate our first CA.
Enter build-ca.bat. This script generates a self-signed certificate for a CA. Such a certificate can be used to create and sign client certificates and thereby authenticate other machines.
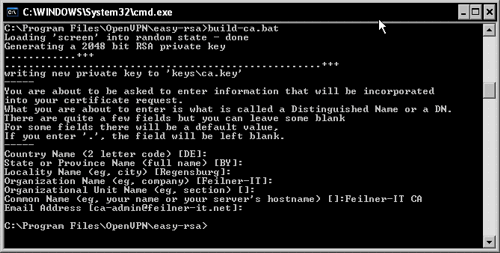
Depending on the data you entered in your vars.bat file, build-ca.bat will suggest different default parameters during the process of generating this certificate. Five of the last seven lines are taken from the variables set in vars.bat. If you edited these parameters, a simple return will do here and the certificate for the CA is generated in the keys directory.
 United States
United States
 Great Britain
Great Britain
 India
India
 Germany
Germany
 France
France
 Canada
Canada
 Russia
Russia
 Spain
Spain
 Brazil
Brazil
 Australia
Australia
 Singapore
Singapore
 Canary Islands
Canary Islands
 Hungary
Hungary
 Ukraine
Ukraine
 Luxembourg
Luxembourg
 Estonia
Estonia
 Lithuania
Lithuania
 South Korea
South Korea
 Turkey
Turkey
 Switzerland
Switzerland
 Colombia
Colombia
 Taiwan
Taiwan
 Chile
Chile
 Norway
Norway
 Ecuador
Ecuador
 Indonesia
Indonesia
 New Zealand
New Zealand
 Cyprus
Cyprus
 Denmark
Denmark
 Finland
Finland
 Poland
Poland
 Malta
Malta
 Czechia
Czechia
 Austria
Austria
 Sweden
Sweden
 Italy
Italy
 Egypt
Egypt
 Belgium
Belgium
 Portugal
Portugal
 Slovenia
Slovenia
 Ireland
Ireland
 Romania
Romania
 Greece
Greece
 Argentina
Argentina
 Netherlands
Netherlands
 Bulgaria
Bulgaria
 Latvia
Latvia
 South Africa
South Africa
 Malaysia
Malaysia
 Japan
Japan
 Slovakia
Slovakia
 Philippines
Philippines
 Mexico
Mexico
 Thailand
Thailand



















