Update: On September 4, 2019, Supermicro released security updates to address vulnerabilities affecting the Baseboard Management Controller (BMC). Administrators can review Supermicro’s Security Advisory and Security Vulnerabilities Table and apply the necessary updates and recommended mitigations.
A cybersecurity firm, Eclypsium reported yesterday that over 47K Supermicro servers have been detected with new vulnerabilities dubbed ‘USBAnywhere’ in their baseboard management controllers (BMCs).
These vulnerabilities “allow an attacker to easily connect to a server and virtually mount any USB device of their choosing to the server, remotely over any network, including the Internet,” Eclypsium mention in their official report.
Issues with BMCs on various Supermicro platforms
The problem arises because of how BMCs on Supermicro X9, X10 and X11 platforms implement virtual media; i.e. they remotely connect a disk image as a virtual USB CD-ROM or floppy drive. On accessing the virtual media service remotely, it allows plaintext authentication, sends most traffic unencrypted, uses a weak encryption algorithm for the rest, and is susceptible to an authentication bypass. Thus, these issues allow an attacker to easily gain access to a server, either by capturing a legitimate user’s authentication packet, using default credentials and in some cases, without any credentials at all.
After the connection is established, the virtual media service allows the attacker to interact with the host system as a raw USB device. This means attackers can attack the server in the same way as if they had physical access to a USB port, such as loading a new operating system image or using a keyboard and mouse to modify the server, implant malware, or even disable the device entirely. The combination of easy access and straightforward attack avenues can allow unsophisticated attackers to remotely attack some of an organization’s most valuable assets.
Analysis of the remote USB authentication
A user can gain access to the virtual media service via a small Java application served on the BMC’s web interface. Further, the Java application connects to the service by listening on TCP port 623 on the BMC. The service, on the other hand, uses a custom packet-based format to authenticate the client and transport USB packets between client and server.
The Eclypsium team analyzed this authentication process and have revealed some issues with it, including:
Plaintext Authentication: While the Java application uses a unique session ID for authentication, the service also allows the client to use a plaintext username and password.
Unencrypted network traffic: Encryption is available but must be requested by the client. The Java application provided with the affected systems use this encryption for the initial authentication packet but then use unencrypted packets for all other traffic.
Weak encryption: When encryption is used, the payload is encrypted with RC4 using a fixed key compiled into the BMC firmware. This key is shared across all Supermicro BMCs. RC4 has multiple published cryptographic weaknesses and has been prohibited from use in TLS (RFC7465).
Authentication Bypass (X10 and X11 platforms only): After a client has properly authenticated to the virtual media service and then disconnected, some of the service’s internal state about that client is incorrectly left intact. As the internal state is linked to the client’s socket file descriptor number, a new client that happens to be assigned the same socket file descriptor number by the BMC’s OS inherits this internal state. In practice, this allows the new client to inherit the previous client’s authorization even when the new client attempts to authenticate with incorrect credentials.
The report highlights, “A scan of TCP port 623 across the Internet revealed 47,339 BMCs from over 90 different countries with the affected virtual media service publicly accessible.”
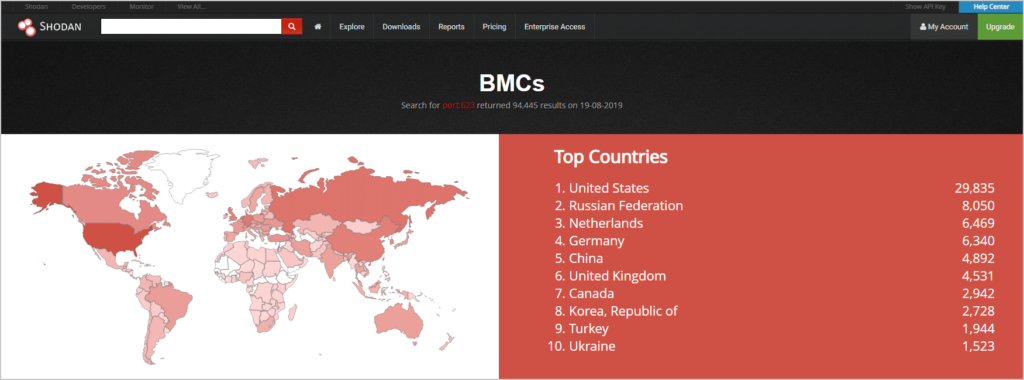
Source: Eclypsium.com
Eclypsium first reported the vulnerability to Supermicro on June 19 and some more additional findings on July 9. Further, on July 29, Supermicro acknowledged the report and developed a fix. On learning that a lot of systems were affected by this vulnerability, Eclypsium notified CERT/CC of the issue, twice in August. On August 23, Eclypsium notified network operators whose networks contain affected, Internet-accessible BMCs. Supermicro also confirmed its intent to publicly release firmware by September 3rd, on August 16.
In order to secure the BMCs, the ones “that are not exposed to the Internet should also be carefully monitored for vulnerabilities and threats. While organizations are often fastidious at applying patches for their software and operating systems, the same is often not true for the firmware in their servers,” the report suggests.
“Just as applying application and OS security updates has become a critical part of maintaining IT infrastructure, keeping abreast of firmware security updates and deploying them regularly is required to defend against casual attacks targeting system firmware,” Eclypsium further suggests.
Also Read: What’s new in USB4? Transfer speeds of upto 40GB/second with Thunderbolt 3 and more
As mitigation to this issue, the company suggests that along with the vendor-supplied updates, organizations should also adopt tools to proactively ensure the integrity of their firmware and identify vulnerabilities, missing protections, and any malicious implants in their firmware.
A user on Hacker News writes, “BMC’s (or the equivalent for whatever vendor you are using) should never be exposed to the internet- they shouldn’t even be on the same network as the rest of the server. Generally speaking. I put them on a completely separate network that has to be VPN’d into explicitly. Having BMC access is as close to having physical access as you can get without actually touching the machine.”
To know more about this news in detail, read Eclypsium’s official report on USBAnywhere.
Other news in security attacks
GitHub now supports two-factor authentication with security keys using the WebAuthn API










![How to create sales analysis app in Qlik Sense using DAR method [Tutorial] Financial and Technical Data Analysis Graph Showing Search Findings](https://hub.packtpub.com/wp-content/uploads/2018/08/iStock-877278574-218x150.jpg)


