686 cybersecurity breaches were reported in the first three months of 2018 alone, with unauthorized intrusion accounting for 38.9% of incidents. And with high-profile data breaches dominating headlines, it’s clear that while modern, complex software architecture might be more adaptable and data-intensive than ever, securing that software is proving a real challenge.
Penetration testing (or pentesting) is a vital component within the cybersecurity toolkit. In theory, it should be at the forefront of any robust security strategy. But it isn’t as simple as just rolling something out with a few emails and new software – it demands people with great skills, as well a culture where stress testing and hacking your own system is viewed as a necessity, not an optional extra.
This is where artificial intelligence comes in – the automation that you can achieve through artificial intelligence could well help make pentesting much easier to do consistently and at scale. In turn, this would help organizations tackle both issues of skills and culture, and get serious about their cybersecurity strategies.
But before we dive deeper into artificial intelligence and pentesting, let’s take a look at where we are now, and the shortcomings of established pentesting methods.
The shortcomings of established methods of pentesting
Typically, pentesting is carried out in 5 stages:
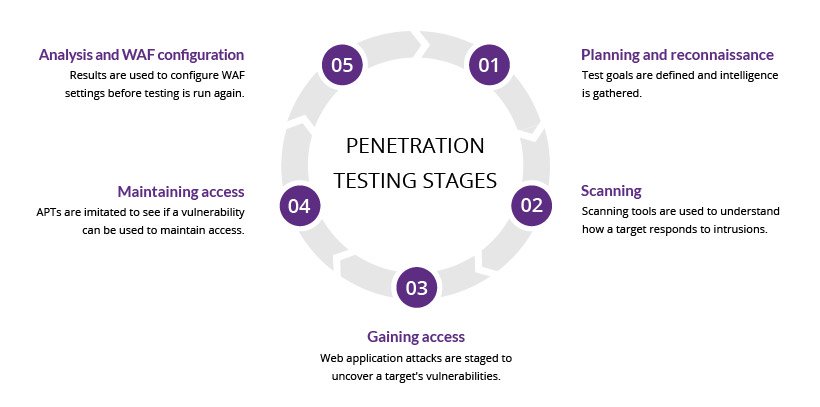
Source: Incapsula
Every one of these stages, when carried out by humans, opens up the chance of error. Yes, software is important, but contextual awareness and decisions are required..
This process, then, provides plenty of opportunities for error. From misinterpreting data – like thinking a system is secure, when actually it isn’t – to taking care of evidence and thoroughly and clearly recording the results of pentests, even the most experienced pentester will get things wrong.
But even if you don’t make any mistakes, this whole process is hard to do well at scale. It requires a significant amount of time and energy to test a piece of software, which, given the pace of change created by modern processes, makes it much harder to maintain the levels of rigor you ultimately want from pentesting.
This is where artificial intelligence comes in.
The pentesting areas that artificial intelligence can impact
Let’s dive into the different stages of pentesting that AI can impact.
#1 Reconnaissance Stage
The most important stage in pentesting is the Reconnaissance or information gathering stage. As rightly said by many in cybersecurity, “The more information gathered, the higher the likelihood of success.” Therefore, a significant amount of time should be spent obtaining as much information as possible about the target.
Using AI to automate this stage would provide accurate results as well as save a lot of time invested. Using a combination of Natural Language Processing, Computer Vision, and Artificial Intelligence, experts can identify a wide variety of details that can be used to build a profile of the company, its employees, the security posture, and even the software/hardware components of the network and computers.
#2 Scanning Stage
Comprehensive coverage is needed In the scanning phase. Manually scanning through thousands if systems in an organization is not ideal. NNor is it ideal to interpret the results returned by scanning tools. AI can be used to tweak the code of the scanning tools to scan systems as well as interpret the results of the scan. It can help save pentesters time and help in the overall efficiency of the pentesting process.
AI can focus on test management and the creation of test cases automatically that will check if a particular program can be tagged having security flaw. They can also be used to check how a target system responds to an intrusion.
#3 Gaining and Maintaining access stage
Gaining access phase involves taking control of one or more network devices in order to either extract data from the target, or to use that device to then launch attacks on other targets. Once a system is scanned for vulnerabilities, the pentesters need to ensure that the system does not have any loopholes that attackers can exploit to get into the network devices. They need to check that the network devices are safely protected with strong passwords and other necessary credentials.
AI-based algorithms can try out different combinations of passwords to check if the system is susceptible for a break-in. The algorithms can be trained to observe user data, look for trends or patterns to make inferences about possible passwords used.
Maintaining access focuses on establishing other entry points to the target. This phase is expected to trigger mechanisms, to ensure that the penetration tester’s security when accessing the network. AI-based algorithms should be run at equal intervals to time to guarantee that the primary path to the device is closed. The algorithms should be able to discover backdoors, new administrator accounts, encrypted channels, new network access channels, and so on.
#4 Covering Tracks And Reporting
The last stage tests whether an attacker can actually remove all traces of his attack on the system. Evidence is most often stored in user logs, existing access channels, and in error messages caused by the infiltration process. AI-powered tools can assist in the discovery of hidden backdoors and multiple access points that haven’t been left open on the target network; All of these findings should be automatically stored in a report with a proper timeline associated with every attack done.
A great example of a tool that efficiently performs all these stages of pentesting is CloudSEK’s X-Vigil. This tool leverages AI to extract data, derive analysis and discover vulnerabilities in time to protect an organization from data breach.
Manual vs automated vs AI-enabled pentesting
Now that you have gone through the shortcomings of manual pen testing and the advantages of AI-based pentesting, let’s do a quick side-by-side comparison to understand the difference between the two.
| Manual Testing | Automated Testing | AI enabled pentesting |
| Manual testing is not accurate at all times due to human error | This is more likely to return false positives | AI enabled pentesting is accurate as compared to automated testing |
| Manual testing is time-consuming and takes up human resources.
|
Automated testing is executed by software tools, so it is significantly faster than a manual approach.
|
AI enabled testing does not consume much time. The algorithms can be deployed for thousands of systems at a single instance. |
| Investment is required for human resources.
|
Investment is required for testing tools. | AI will save the investment for human resources in pentesting. Rather, the same employees can be used to perform less repetitive and more efficient tasks |
| Manual testing is only practical when the test cases are run once or twice, and frequent repetition is not required..
|
Automated testing is practical when tools find test vulnerabilities out of programmable bounds | AI-based pentesting is practical in organizations with thousands of systems that need to be tested at once to save time and resources. |
AI-based pentesting tools
Pentoma is an AI-powered penetration testing solution that allows software developers to conduct smart hacking attacks and efficiently pinpoint security vulnerabilities in web apps and servers. It identifies holes in web application security before hackers do, helping prevent any potential security damages.
Pentoma analyzes web-based applications and servers to find unknown security risks.In Pentoma, with each hacking attempt, machine learning algorithms incorporate new vulnerability discoveries, thus continuously improving and expanding threat detection capability.
Wallarm Security Testing is another AI based testing tool that discovers network assets, scans for common vulnerabilities, and monitors application responses for abnormal patterns.
It discovers application-specific vulnerabilities via Automated Threat Verification. The content of a blocked malicious request is used to create a sanitized test with the same attack vector to see how the application or its copy in a sandbox would respond.
With such AI based pentesting tools, pentesters can focus on the development process itself, confident that applications are secured against the latest hacking and reverse engineering attempts, thereby helping to streamline a product’s time to market.
Perhaps it is the increase in the number of costly data breaches or the continually expanding attack and proliferation of sensitive data and the attempt to secure them with increasingly complex security technologies that businesses lack in-house expertise to properly manage.
Whatever be the reason, more organizations are waking up to the fact that if vulnerabilities are not caught in time can be catastrophic for the business. These weaknesses, which can range from poorly coded web applications, to unpatched databases to exploitable passwords to an uneducated user population, can enable sophisticated adversaries to run amok across your business. It would be interesting to see the growth of AI in this field to overcome all the aforementioned shortcomings.
Read Next
5 ways artificial intelligence is upgrading software engineering
Intelligent Edge Analytics: 7 ways machine learning is driving edge computing adoption in 2018
8 ways Artificial Intelligence can improve DevOps










![How to create sales analysis app in Qlik Sense using DAR method [Tutorial] Financial and Technical Data Analysis Graph Showing Search Findings](https://hub.packtpub.com/wp-content/uploads/2018/08/iStock-877278574-218x150.jpg)


