Yesterday, FireEye revealed a new group of hackers named APT38, a financially motivated North Korean regime-backed group responsible for conducting destructive attacks against financial institutions, as well as for some of the world’s largest cyber heists.
FireEye Inc. is a cybersecurity firm that provides products and services to protect against advanced persistent threats and spear phishing.
Earlier this year, FireEye helped Facebook find suspicious accounts linked to Russia and Iran on its platform and also alerted Google of election influence operations linked to Iranian groups.
Now FireEye cybersecurity researchers released a special report titled APT38: Un-usual Suspects, to expose the methods used by the APT38 group. In the report, they said,“Based on observed activity, we judge that APT38’s primary mission is targeting financial institutions and manipulating inter-bank financial systems to raise large sums of money for the North Korean regime.”
The researchers also state that the group has attempted to steal more than $1.1 billion and were also responsible for some of the more high-profile attacks on financial institutions in the last few years. Some of the publicly reported attempted heists attributable to APT38 include:
- Vietnam TP Bank in December 2015
- Bangladesh Bank in February 2016
- Far Eastern International Bank in Taiwan in October 2017
- Bancomext in January 2018
- Banco de Chile in May 2018
Sandra Joyce, FireEye’s vice president of global intelligence says, “The hallmark of this group is that it deploys destructive malware after stealing money from an organization, not only to cover its tracks, but [also] in order to distract defenders, complicate the incident response process, and gain time to get out the door.”
Some details of the APT38 targeting
- Since at least 2014, APT38 has conducted operations in more than 16 organizations in at least 11 countries. The total number of organizations targeted by APT38 may be even higher when considering the probable low incident reporting rate from affected organizations.
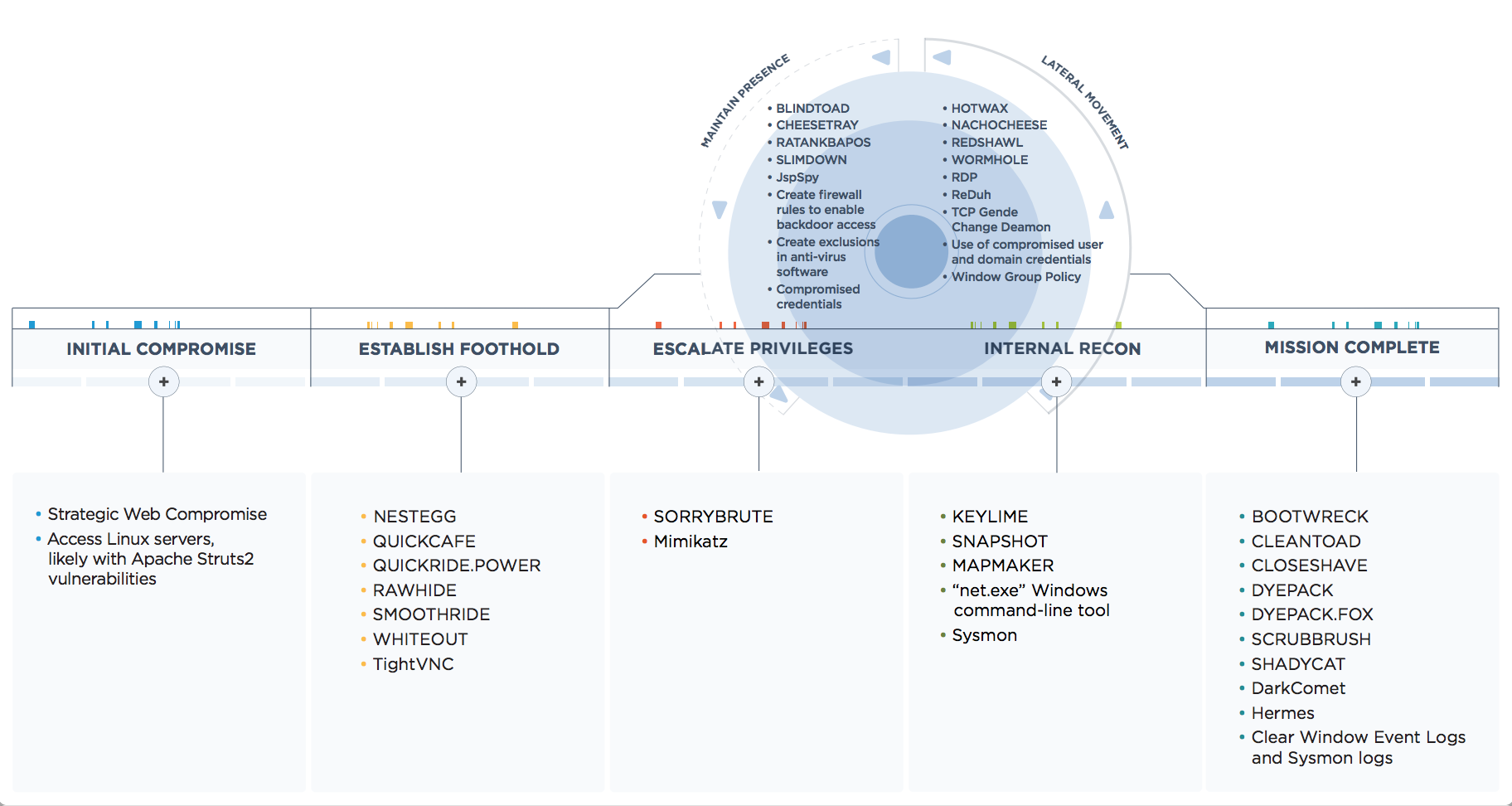
- The group is careful, calculated, and has demonstrated a desire to maintain access to a victim environment for as long as necessary to understand the network layout, required permissions, and system technologies to achieve its goals.
- On average, they have observed that APT38 remain within a victim network for approximately 155 days, with the longest time within a compromised environment believed to be almost two years.
- In just the publicly reported heists alone, APT38 has attempted to steal over $1.1 billion dollars from financial institutions.
FireEye researchers believe that APT38’s financial motivation, unique toolset, tactics, techniques and procedures (TTPs) observed during their carefully executed operations are distinct enough to be tracked separately from other North Korean cyber activity. The APT38 group overlaps characteristics with other operations, known as ‘Lazarus’ and the actor they call as TEMP.Hermit.
On Tuesday, the U.S. government released details on malware it alleges Pyongyang’s computer operatives have used to fraudulently withdraw money from ATMs in various countries.
The unmasking of APT38 comes weeks after the Justice Department announced charges against Park Jin Hyok, a North Korean computer programmer, in connection with the 2014 hack of Sony Pictures and the 2017 WannaCry ransomware attack. According to Jacqueline O’Leary, a senior threat intelligence analyst at FireEye, Park has likely contributed to both APT38 and TEMP.Hermit operations.
However, the North Korean government has denied allegations that it sponsors such hacking.
Read Next
Reddit posts an update to the FireEye’s report on suspected Iranian influence operation
Facebook COO, Sandberg’s Senate testimony
Google’s Protect your Election program










![How to create sales analysis app in Qlik Sense using DAR method [Tutorial] Financial and Technical Data Analysis Graph Showing Search Findings](https://hub.packtpub.com/wp-content/uploads/2018/08/iStock-877278574-218x150.jpg)


