Creating virtual machines on Azure gives you on-demand, high-scale, secure, virtualized infrastructure using Windows Server. Virtual machine helps you deploy and scale applications easily. In this article, we will learn how to run an Azure Virtual Machine.
This tutorial is an excerpt from the book, Hands-On Networking with Azure, written by Mohamed Waly. This book will help you efficiently monitor, diagnose, and troubleshoot Azure Networking.
Creating an Azure VM is a very straightforward process – all you have to do is follow the given steps:
- Navigate to the Azure portal and search for Virtual Machines, as shown in the following screenshot:
Figure 3.1: Searching for Virtual Machines
- Once the VM blade is opened, you can click on +Add to create a new VM, as shown in the following screenshot:
Figure 3.2: Virtual Machines blade
- Once you have clicked on +Add, a new blade will pop up where you have to search for and select the desired OS for the VM, as shown in the following screenshot:
Figure 3.3: Searching for Windows Server 2016 OS for the VM
- Once the OS is selected, you need to select the deployment model, whether that be Resource Manager or Classic, as shown in the following screenshot:
Figure 3.4: Selecting the deployment model
- Once the deployment model is selected, a new blade will pop up where you have to specify the following:
- Name: Specify the name of the VM.
- VM disk type: Specify whether the disk type will be SSD or HDD. Consider that SSD will offer consistent, low-latency performance, but will incur more charges. Note that this option is not available for the Classic model in this blade, but is available in the Configure optional features blade.
- User name: Specify the username that will be used to log on the VM.
- Password: Specify the password, which must be between 12 and 123 characters long and must contain three of the following: one lowercase character, one uppercase character, one number, and one special character that is not or -.
- Subscription: This specifies the subscription that will be charged for the VM usage.
- Resource group: This specifies the resource group within which the VM will exist.
- Location: Specify the location in which the VM will be created. It is recommended that you select the nearest location to you.
- Save money: Here, you specify whether you own Windows Server Licenses with active Software Assurance (SA). If you do, Azure Hybrid Benefit is recommended to save compute costs.
For more information about Azure Hybrid Benefit, you can check this
page.
Figure 3.5: Configure the VM basic settings
- Once you have clicked on OK, a new blade will pop up where you have to specify the VM size so that the VMs series can select the one that will fulfil your needs, as shown in the following screenshot:
Figure 3.6: Select the VM size
- Once the VM size has been specified, you need to specify the following settings:
- Availability set: This option provides High availability for the VM by setting the VMs within the same application and availability set. Here, the VMs will be in different fault and update domains, granting the VMs high availability (up to 99.95% of Azure SLA).
- Use managed disks: Enable this feature to have Azure automatically manage the availability of disks to provide data redundancy and fault tolerance without creating and managing storage accounts on your own. This setting is not available in the Classic model.
- Virtual network: Specify the virtual network to which you want to assign the VM.
- Subnet: Select the subnet within the virtual network that you specified earlier to assign the VM to.
- Public IP address: Either select an existing public IP address or create a new one.
- Network security group (firewall): Select the NSG you want to assign to the VM NIC. This is called endpoints in the Classic model.
- Extensions: You can add more features to the VM using extensions, such as configuration management, antivirus protection, and so on.
- Auto-shutdown: Specify whether you want to shut down your VM daily or not; if you do, you can set a schedule. Considering that this option will help you saving compute cost especially for dev and test scenarios. This is not available in the Classic model.
- Notification before shutdown: Check this if you enabled Auto-shutdown and want to subscribe for notifications before the VM shuts down. This is not available in the Classic model.
- Boot diagnostics: This captures serial console output and screenshots of the VM running on a host to help diagnose start up issues.
- Guest OS diagnostics: This obtains metrics for the VM every minute; you can use these metrics to create alerts and stay informed of your applications.
- Diagnostics storage account: This is where metrics are written, so you can analyze them with your own tools.
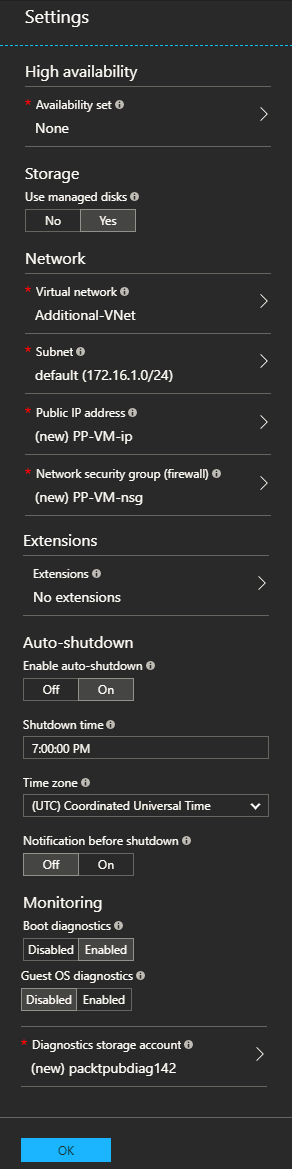
Figure 3.7: Specify more settings for the VM
Enabling Boot diagnostics and Guest diagnostics will incur more charges since the diagnostics will need a dedicated storage account to store their data.
- Finally, once you are done with its settings, Azure will validate those you have specified and summarize them, as shown in the following screenshot:
Figure 3.8: VM Settings Summary
- Once clicked on, Create the VM will start the creation process, and within minutes the VM will be created.
- Once the VM is created, you can navigate to the Virtual Machines blade to open the VM that has been created, as shown in the following screenshot:
Figure 3.9: The created VM overview
- To connect to the VM, click on Connect, where a pre-configured RDP file with the required VM information will be downloaded.
- Open the RDP file. You will be asked to enter the username and password you specified for the VM during its configuration, as shown in the following screenshot:
Figure 3.10: Entering the VM credentials
- Voila! You should now be connected to the VM.
Azure VMs networking
There are many network configurations that can be done for the VM. You can add additional NICs, change the private IP address, set a private or public IP address to be either static or dynamic, and you can change the inbound and outbound security rules.
Adding inbound and outbound rules
Adding inbound and outbound security rules to the VM NIC is a very simple process; all you need to do is follow these steps:
- Navigate to the desired VM.
- Scroll down to Networking, under SETTINGS, as shown in the following screenshot:
Figure 3.11: VM networking settings
- To add inbound and outbound security rules, you have to click on either Add inbound or Add outbound.
- Once clicked on, a new blade will pop up where you have to specify settings using the following fields:
- Service: The service specifies the destination protocol and port range for this rule. Here, you can choose a predefined service, such as RDP or SSH, or provide a custom port range.
- Port ranges: Here, you need to specify a single port, a port range, or a comma-separated list of single ports or port ranges.
- Priority: Here, you enter the desired priority value.
- Name: Specify a name for the rule here.
- Description: Write a description for the rule that relates to it here.
Figure 3.12: Adding an inbound rule
- Once you have clicked OK, the rule will be applied. Note that the same process applies when adding an outbound rule.
Adding an additional NIC to the VM
Adding an additional NIC starts from the same blade as adding inbound and outbound rules. To add an additional NIC, you have to follow the given steps:
- Before adding an additional NIC to the VM, you need to make sure that the VM is in a Stopped (Deallocated) status.
- Navigate to Networking on the desired VM.
- Click on Attach network interface, and a new blade will pop up. Here, you have to either create a network interface or select an existing one. If you are selecting an existing interface, simply click on OK and you are done. If you are creating a new interface, click on Create network interface, as shown in the following screenshot:
Unlock access to the largest independent learning library in Tech for FREE!
Get unlimited access to 7500+ expert-authored eBooks and video courses covering every tech area you can think of.
Renews at $19.99/month. Cancel anytime
Figure 3.13: Attaching network interface
- A new blade will pop up where you have to specify the following:
-
- Name: The name of the new NIC.
- Virtual network: This field will be grayed out because you cannot attach a VM's NIC to different virtual networks.
- Subnet: Select the desired subnet within the virtual network.
- Private IP address assignment: Specify whether you want to allocate this IP dynamically or statically.
- Network security group: Specify an NSG to be assigned to this NIC.
- Private IP address (IPv6): If you want to assign an IPv6 to this NIC, check this setting.
- Subscription: This field will be grayed out because you cannot have a VM's NIC in a different subscription.
- Resource group: Specify the resource group to which the NIC will exist.
- Location: This field will be grayed out because you cannot have VM NICs in different locations.
Figure 3.14: Specify the NIC settings
- Once you are done, click Create.
- Once the network interface is created, you will return to the previous blade. Here, you need to specify the NIC you just created and click on OK, as shown in the following screenshot:
Figure 3.15: Attaching the NIC
Configuring the NICs
The Network Interface Cards (NICs) include some configuration that you might be interested in. They are as follows:
- To navigate to the desired NIC, you can search for the network interfaces blade, as shown in the following screenshot:
Figure 3.16: Searching for network interfaces blade
- Then, the blade will pop up, from which you can select the desired NIC, as shown in the following screenshot:
Figure 3.17: Select the desired NIC
- You can also navigate back to the VM via | Networking | and then click on the desired NIC, as shown in the following screenshot:
Figure 3.18: The VM NIC
- To configure the NIC, you need to follow the given steps:
- Once the NIC blade is opened, navigate to IP configurations, as shown in the following screenshot:
Figure 3.19: NIC blade overview
-
- To enable IP forwarding, click on Enabled and then click Save. Enabling this feature will cause the NIC to receive traffic that is not destined to its own IP address. Traffic will be sent with a different source IP.
- To add another IP to the NIC, click on Add, and a new blade will pop up, for which you have to specify the following:
- Name: The name of the IP.
- Type: This field will be grayed out because a primary IP already exists. Therefore, this one will be secondary.
- Allocation: Specify whether the allocation method is static or dynamic.
- IP address: Enter the static IP address that belongs to the same subnet that the NIC belongs to. If you have selected dynamic allocation, you cannot enter the IP address statically.
- Public IP address: Specify whether or not you need a public IP address for this IP configuration. If you do, you will be asked to configure the required settings.
Figure 3.20: Configure the IP configuration settings
-
- Click on Configure required settings for the public IP address and a new blade will pop up from which you can select an existing public IP address or create a new one, as shown in the following screenshot:
Figure 3.21: Create a new public IP address
-
- Click on OK and you will return to the blade, as shown in Figure 3.20, with the following warning:
Figure 3.22: Warning for adding a new IP address
- In this case, you need to plan for the addition of a new IP address to ensure that the time the VM is restarted is not during working hours.
Azure VNets considerations for Azure VMs
Building VMs in Azure is a common task, but to do this task well, and to make it operate properly, you need to understand the considerations of Azure VNets for Azure VMs. These considerations are as follows:
- Azure VNets enable you to bring your own IPv4/IPv6 addresses and assign them to Azure VMs, statically or dynamically
- You do not have access to the role that acts as DHCP or provides IP addresses; you can only control the ranges you want to use in the form of address ranges and subnets
- Installing a DHCP role on one of the Azure VMs is currently unsupported; this is because Azure does not use traditional Layer-2 or Layer-3 topology, and instead uses Layer-3 traffic with tunneling to emulate a Layer-2 LAN
- Private IP addresses can be used for internal communication; external communication can be done via public IP addresses
- You can assign multiple private and public IP addresses to a single VM
- You can assign multiple NICs to a single VM
- By default, all the VMs within the same virtual network can communicate with each other, unless otherwise specified by an NSG on a subnet within this virtual network
- The network security group (NSG) can sometimes cause an overhead; without this overhead, however, all VMs within the same subnet would communicate with each other
- By default, an inbound security rule is created for remote desktops for Windows-based VMs, and SSH for Linux-based VMs
- The inbound security rules are first applied on the NSG of the subnet and then the VM NIC NSG – for example, if the subnet's NSG allows HTTP traffic, it will pass through it; however, it may not reach its destination if the VM NIC NSG does not allow it
- The outbound security rules are applied for the VM NIC NSG first, and then applied on the subnet NSG
- Multiple NICs assigned to a VM can exist in different subnets
- Azure VMs with multiple NICs in the same availability set do not have to have the same number of NICs, but the VMs must have at least two NICs
- When you attach an NIC to a VM, you need to ensure that they exist in the same location and subscription
- The NIC and the VNet must exist in the same subscription and location
- The NIC's MAC address cannot be changed until the VM to which the NIC is assigned is deleted
- Once the VM is created, you cannot change the VNet to which it is assigned; however, you can change the subnet to which the VM is assigned
- You cannot attach an existing NIC to a VM during its creation, but you can add an existing NIC as an additional NIC
- By default, a dynamic public IP address is assigned to the VM during creation, but this address will change if the VM is stopped or deleted; to ensure it will not change, you need to ensure its IP address is static
- In a multi-NIC VM, the NSG that is applied to one NIC does not affect the others
If you found this post useful, do check out the book Hands-On Networking with Azure, to design and implement Azure Networking for Azure VMs.
Read More
Introducing Azure Sphere – A secure way of running your Internet of Things devices
Learn Azure Serverless computing for free: Download e-book
 United States
United States
 Great Britain
Great Britain
 India
India
 Germany
Germany
 France
France
 Canada
Canada
 Russia
Russia
 Spain
Spain
 Brazil
Brazil
 Australia
Australia
 Singapore
Singapore
 Canary Islands
Canary Islands
 Hungary
Hungary
 Ukraine
Ukraine
 Luxembourg
Luxembourg
 Estonia
Estonia
 Lithuania
Lithuania
 South Korea
South Korea
 Turkey
Turkey
 Switzerland
Switzerland
 Colombia
Colombia
 Taiwan
Taiwan
 Chile
Chile
 Norway
Norway
 Ecuador
Ecuador
 Indonesia
Indonesia
 New Zealand
New Zealand
 Cyprus
Cyprus
 Denmark
Denmark
 Finland
Finland
 Poland
Poland
 Malta
Malta
 Czechia
Czechia
 Austria
Austria
 Sweden
Sweden
 Italy
Italy
 Egypt
Egypt
 Belgium
Belgium
 Portugal
Portugal
 Slovenia
Slovenia
 Ireland
Ireland
 Romania
Romania
 Greece
Greece
 Argentina
Argentina
 Netherlands
Netherlands
 Bulgaria
Bulgaria
 Latvia
Latvia
 South Africa
South Africa
 Malaysia
Malaysia
 Japan
Japan
 Slovakia
Slovakia
 Philippines
Philippines
 Mexico
Mexico
 Thailand
Thailand




































