Last week, Cisco announced of a severe vulnerability in the web-based management interface of its Small Business RV320 and RV325 Dual Gigabit WAN VPN Routers. This vulnerability could easily allow an unauthenticated, remote attacker to retrieve sensitive information.
Cisco in their report, mention that this vulnerability is due to the improper access controls for URLs. An attacker could easily exploit this vulnerability by connecting to the affected device via HTTP or HTTPS and requesting specific URLs. A successful exploit could allow the attacker to download the router configuration or detailed diagnostic information.
Cisco routers vulnerable to CVE-2019-1653
According to Bad packets report, they scanned around 15,309 unique IPv4 hosts and determined 9,657 Cisco RV320/RV325 routers are vulnerable to CVE-2019-1653. Their report states,
- 6,247 out of 9,852 Cisco RV320 routers scanned are vulnerable (1,650 are not vulnerable and 1,955 did not respond to our scans)
- 3,410 out of 5,457 Cisco RV325 routers scanned are vulnerable (1,027 are not vulnerable and 1,020 did not respond to our scans)
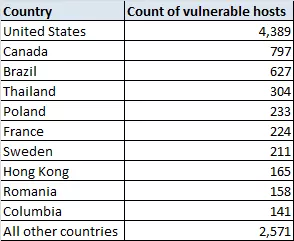
Source: Bad packets report
This vulnerability also affects Cisco Small Business RV320 and RV325 Dual Gigabit WAN VPN Routers running Firmware Releases 1.4.2.15 and 1.4.2.17. Cisco has also released firmware updates to address this vulnerability. However, they mention, there are no workarounds that address this vulnerability.
To know about this news in detail, visit Cisco’s official website.
Read Next
Cisco and Huawei Routers hacked via backdoor attacks and botnets
Dropbox purchases workflow and eSignature startup ‘HelloSign’ for $250M










![How to create sales analysis app in Qlik Sense using DAR method [Tutorial] Financial and Technical Data Analysis Graph Showing Search Findings](https://hub.packtpub.com/wp-content/uploads/2018/08/iStock-877278574-218x150.jpg)


