A vulnerability in Mac’s Zoom Client allows any malicious website to initiate users’ camera and forcibly join a Zoom call without their authority. This vulnerability was publicly disclosed by security researcher, Jonathan Leitschuh, today.
The flaw exposes up to 750,000 companies around the world using the video conferencing app on their Macs, to conduct day-to-day business activities. It also allows a website to launch a DoS (Denial of Service) attack on Macs by repeatedly joining a user to an invalid call. Even if one tries to uninstall the app from their devices, it can even re-install the app without user’s permission with the help of a localhost web server on the machine that should have installed the app at least once.
I saw something similar with GotoMeeting on the Mac. I'd uninstall, but then a few weeks later a new version would be installed, unannounced. If I didn't notice for a month or two, I'd have 5 or 6 *different versions* of GotoMeeting installed.
— Oldham-Made (@OldhamMade) July 9, 2019
“This vulnerability leverages the amazingly simple Zoom feature where you can just send anyone a meeting link (for example https://zoom.us/j/492468757) and when they open that link in their browser their Zoom client is magically opened on their local machine”, Leitschuh writes.
Leitschuh said that the vulnerability was responsibly disclosed on March 26, this year. This means the company had 90 days to fix this issue based on the disclosure policy. He had suggested a ‘quick fix’ which Zoom could have implemented by simply changing their server logic.
However, Zoom first took 10 days to confirm the vulnerability and held a meeting about how the vulnerability would be patched, only 18 days before the end of the 90-day public disclosure deadline, i.e. June 11th, 2019. A day before the public disclosure, Zoom had only implemented the quick fix solution. “An organization of this profile and with such a large user base should have been more proactive in protecting their users from attack”, Leitschuh says.
Leitschuh also mentioned the Tenable Remote Code Execution in Zoom security vulnerability which was only patched within the last 6 months. “Had the Tenable vulnerability been combined with this vulnerability it would have allowed RCE against any computer with the Zoom Mac client installed. If a similar future vulnerability were to be found, it would allow any website on the internet to achieve RCE on the user’s machine”, Leitschuh adds.
According to ZDNet, “Leitschuh also pointed out to Zoom that a domain it used for sending out updates was about to expire before May 1, but the domain was renewed in late April”.
In a statement to The Verge, Zoom said, the local webserver was developed “to save users some clicks after Apple changed its Safari web browser in a way that requires Zoom users to confirm that they want to launch Zoom each time”.
Zoom defended their “workaround” and said it is a “legitimate solution to poor user experience, enabling our users to have seamless, one-click-to-join meetings, which is our key product differentiator.” The company said it would do some minor tweaking to the app this month. “Zoom will save users’ and administrators’ preferences for whether the video will be turned on, or not when they first join a call”, the company said.
Part of Zoom's response below. Basically: an update to Safari (probably for security?) added an extra click to joining a meeting. So Zoom added a whole damn, undisclosed, running webserver to your computer to Save You A Click. And it isn't sorry.
Really. pic.twitter.com/GoSHzAci3Y
— Dieter Bohn (@backlon) July 9, 2019
This move by Zoom is unfair towards users where they have to turn their cameras off and the company just escapes with a minor change to the app for such a serious security lapse issue where they should have taken a major step.
Many are unhappy with the way Zoom is handling this vulnerability.
This Zoom client vuln on Mac is actually pretty bad, and it seems to have been handled poorly by Zoom. https://t.co/3jSmPHPqim
— Chad Loder ✸ (@chadloder) July 8, 2019
I found this a few months ago when I was having problems with Zoom crashing on my Mac and despite deleting and rebooting it would dutifully reinstall and start up every time I clicked a meeting link. What a horribly skeevy app!
— Jessica🏳️🌈 (@ticky) July 9, 2019
Users can patch the camera issue by themselves by updating their Mac and disabling the setting that allows Zoom to turn your camera on when joining a meeting.
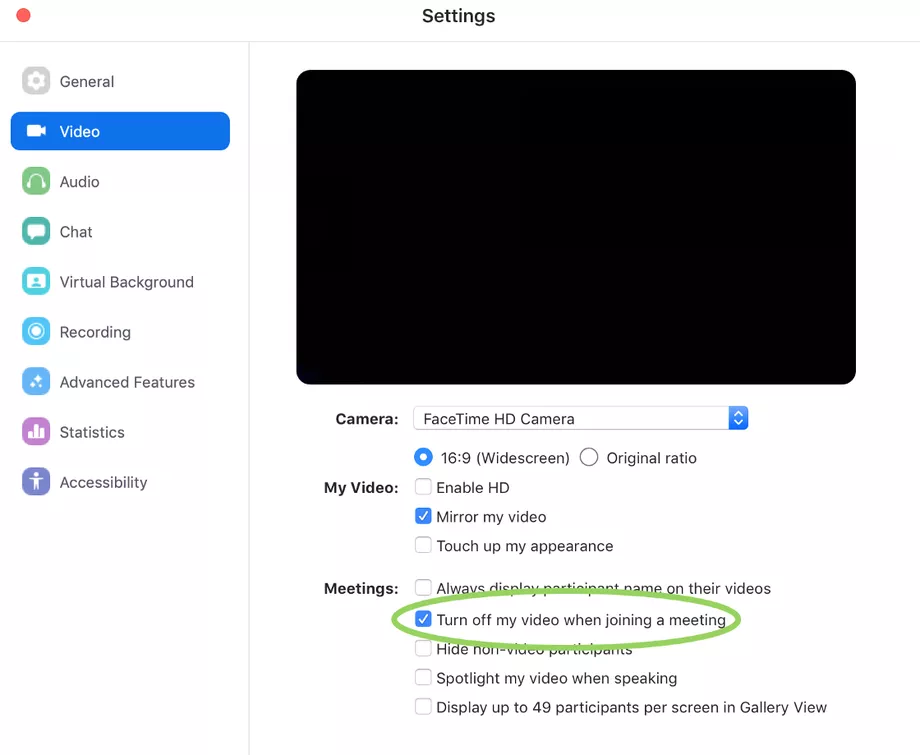
As mentioned earlier, the vulnerability may re-install the applications; hence, users are advised to run some terminal commands to turn off their web server. Leitschuh has explained these commands in detail in his blog post on Medium.










![How to create sales analysis app in Qlik Sense using DAR method [Tutorial] Financial and Technical Data Analysis Graph Showing Search Findings](https://hub.packtpub.com/wp-content/uploads/2018/08/iStock-877278574-218x150.jpg)


