Earlier this week, Mozilla fixed a zero-day vulnerability that was being actively exploited by attackers. It released another security update yesterday when the Coinbase Security team detected a second zero-day vulnerability in Firefox. This update has landed in Firefox 67.0.4 and Firefox ESR 60.7.2.
The two zero-day vulnerabilities
The first one was a type confusion vulnerability tracked as CVE-2019-11707 that occurs “when manipulating JavaScript objects due to issues in Array.pop. This can allow for an exploitable crash.” It enables an attacker to run malicious code inside Firefox’s native process. This vulnerability was reported by both Coinbase Security team and Samuel Groß, a security researcher with Google Project Zero security team. Groß has reported the vulnerability on Bugzilla back in April 15th.
I don't have any insights into the active exploitation part. I found and then reported the bug on April 15. The first public fix then landed about a week ago (sec fixes are held back until close to the next release): https://t.co/O34f9dou3E https://t.co/K6GfZN1XkH
— Samuel Groß (@5aelo) June 19, 2019
Sharing the implications of the vulnerability, the tech researcher said, “the bug can be exploited for RCE [remote code execution] but would then need a separate sandbox escape to run code on an underlying operating system. However, most likely it can also be exploited for UXSS [universal cross-site scripting] which might be enough depending on the attacker’s goals.”
The second zero-day vulnerability was described as “sandbox escape using Prompt:Open” and is assigned CVE-2019-11708. This highly-critical vulnerability enables the escape of malware from the Firefox protected process and its execution on the targeted host. “Insufficient vetting of parameters passed with the Prompt:Open IPC message between child and parent processes can result in the non-sandboxed parent process opening web content chosen by a compromised child process,” the advisory page reads.
The Coinbase attack
Not much detail was out about these attacks and vulnerabilities until yesterday when Martin Phil, Chief Information Security Officer at Coinbase, and his team detected an attack targeting Coinbase employees. Coinbase also said that the attacker might have targeted other cryptocurrency organizations as well. It is now notifying the organizations that it believes have been possibly targeted.
1/ A little more context on the Firefox 0-day reports. On Monday, Coinbase detected & blocked an attempt by an attacker to leverage the reported 0-day, along with a separate 0-day firefox sandbox escape, to target Coinbase employees.
— Philip Martin (@SecurityGuyPhil) June 19, 2019
Fortunately, the attack was detected before it was able to do any damage. If it had been left undetected, the attacker could have gained access to the Coinbase backend network and stole funds from exchanges. Phil in his tweets also shared a couple of Indicators of Compromise (IOC) that will give the indication whether a system is affected or not.
5/ Hashes (sha1):
b639bca429778d24bda4f4a40c1bbc64de46fa79
23017a55b3d25a2597b7148214fd8fb2372591a5C2 IPs:
89.34.111.113:443
185.49.69.210:80— Philip Martin (@SecurityGuyPhil) June 19, 2019
Vitali Kremez who specializes in Information Security, Malware Hunting & Carding, Cybercrime Intelligence, speculated that these IOCs were linked to a username “powercat”.
2019-06-19: 🌊Possible Similarities b/w Mach-O
& PE32 Payloads (Linked to #Firefox #0day #IOCs) | #Malware #Stealer via #PowerCat (C2: 89.34.111. 113) | Signed 🔏 | "powercat.ps1"
h/t @SecurityGuyPhil
✅Pushed IOCs & notes to Git for additional review –https://t.co/hlEUsu0C0p pic.twitter.com/7f3PPLcSJg— Vitali Kremez (@VK_Intel) June 20, 2019
Going by the IOCs, we can say that the attacker would have sent a spear-phishing email to lure victims to a web page. So, if the victims were using a vulnerable Firefox version, the web page would have downloaded and installed the malware on their systems.
The macOS backdoor attack
Not only cryptocurrency organizations, it looks like the attacker has also targeted other Firefox users as well. Yesterday, Patrick Wardle, a macOS security expert published an analysis of a Mac malware. This malware was sent by a user who claimed that it was installed in his fully updated Mac through Firefox’s zero-day vulnerability. Here’s how the email sent by the attacker to this user looked like:
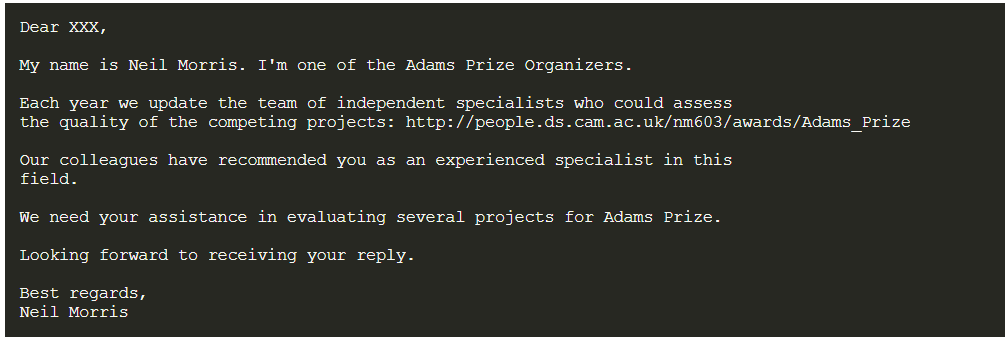
Source: Objective-See
The malware that was installed on the user’s system was called Finder.app, the hash of which completely matched with one of the hashes provided by Martin.
This news sparked a discussion on Hacker News. Many users found it unsettling that Mozilla took two months to deliver the security patch to fix a very crucial bug report. “Really, that Mozilla would let a reported RCE vulnerability simmer for two months until it bit someone would seem to reflect very poorly on their priorities and competence,” a user commented.
Others were rather interested to know how Coinbase discovered this attack. A user commented, “I am more interested in how Coinbase employees discovered the attack. I am assuming nobody clicked the suspicious link and instead took it to a vm for reversing and analysis. It would have been game over if the exploit was actually executed on a non-sandboxed machine.”
Read Next
Firefox 67 enables AV1 video decoder ‘dav1d’, by default on all desktop platforms










![How to create sales analysis app in Qlik Sense using DAR method [Tutorial] Financial and Technical Data Analysis Graph Showing Search Findings](https://hub.packtpub.com/wp-content/uploads/2018/08/iStock-877278574-218x150.jpg)


